In penetration testing first step is how we can bypass AV & make our payload FUD. Previously we saw that we can bypass AV using Veil.At that time we used python module.In veil there are four types of payload.C,C#,powershell and python. Today we use powershell module.
If you don`t aware about powershell ; then you can google it.It`s windows based scripting language like bash in linux.Most of AV cannot detect it.We use SET powershell module to bypass AV; you can also use veil module.
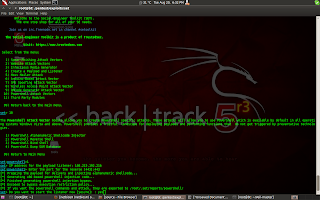
cd /pentest/exploits/set/
./setoolkit
type 1 which is social engineering attack
After that type 10.
Then give your i.p. & port to connect reverse shell.
Now in figure you can see that it has been generated & stored in to /root/.set/reports/powershell . And we also start metasploit listener.If victim paste our generated payload in cmd then we can get meterpreter shell. But i think it`s hard to tell someone to copy something & paste into cmd. So we will create batch file of our payload.
(1)open x86_powershell_injection.txt file from /root/.set/reports/powershell.
(2)Add path of powershell in first line. For example your code is starting from powershell word just put C:\\windows/system32/windowspowershell/v1.0/ before it.
(3)If you want to hide text during execution put @echo off at start of script.
(4)copy all code from x86_powershell_injection.txt
(5)Create new file & paste code
(6)Save this file as .bat extension and send to victim
As soon as he open file we can get shell.
If you don`t aware about powershell ; then you can google it.It`s windows based scripting language like bash in linux.Most of AV cannot detect it.We use SET powershell module to bypass AV; you can also use veil module.
cd /pentest/exploits/set/
./setoolkit
type 1 which is social engineering attack
After that type 10.
Then give your i.p. & port to connect reverse shell.
Now in figure you can see that it has been generated & stored in to /root/.set/reports/powershell . And we also start metasploit listener.If victim paste our generated payload in cmd then we can get meterpreter shell. But i think it`s hard to tell someone to copy something & paste into cmd. So we will create batch file of our payload.
Create Batch file of our Payload.
(1)open x86_powershell_injection.txt file from /root/.set/reports/powershell.
(2)Add path of powershell in first line. For example your code is starting from powershell word just put C:\\windows/system32/windowspowershell/v1.0/ before it.
(3)If you want to hide text during execution put @echo off at start of script.
(4)copy all code from x86_powershell_injection.txt
(5)Create new file & paste code
(6)Save this file as .bat extension and send to victim
As soon as he open file we can get shell.